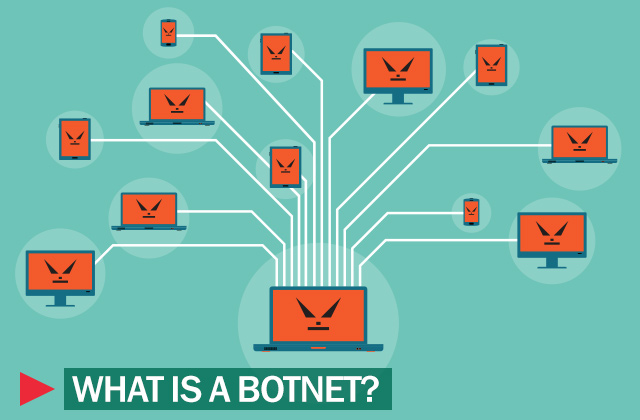
In this article, we will discuss the important information about the Botnets. Botnet word derived from ro-bot. First Botnet was created in 1993 by Jeff Fisher. This bot was used as feature of Internet Relay Chart(IRC). Any system or host which is compromised by bot become the part of botnet attack. When a number of Computers, Mobile Devices or IOT devices security breached than its called botnet. In simple words, when a hacker or group of hackers break the security of large number of devices and gain access to these devices. This activity will call the botnets.
Credit Kaspersky
From the hackers point of view, botnet is very important to gain the access of large number of devices. Hacker use the Command & Control(C&C) program on target sever where he or she will launch the attacks the devices which are connected to the server.One intersting fact about botnet is that a hacker can automate the cyber attack withing 15 seconds if he or she doing the botnet attacks. In the survey of Kasper Sky suggests that DDOS attack can reach the margin of 95% out of total cyber security attacks without information of hackers. Hackers do not attack the target system or device directly.
History of Botnet: In 2000, first botnet attack done by the hacker name Khan K Smith. In this attack, he sent 1.25 millions emails from legitimate websites. From this attack, he gained the sensitive information like customer credit and bank account details. In the end, he earned $3 million from Earthlink Company with this attack and then Earthlink company sued him $25 million.
How to prevent the Botnet: Here are few steps to stop the botnet attacks
Source: https://securityintelligence.com/thingbots-the-future-of-botnets-in-the-internet-of-things/
Source: https://www.esecurityplanet.com/trends/article.php/3920881/11-Ways-to-Combat-Botnets-the-Invisible-Threat.htm

Credit Kaspersky
From the hackers point of view, botnet is very important to gain the access of large number of devices. Hacker use the Command & Control(C&C) program on target sever where he or she will launch the attacks the devices which are connected to the server.One intersting fact about botnet is that a hacker can automate the cyber attack withing 15 seconds if he or she doing the botnet attacks. In the survey of Kasper Sky suggests that DDOS attack can reach the margin of 95% out of total cyber security attacks without information of hackers. Hackers do not attack the target system or device directly.
History of Botnet: In 2000, first botnet attack done by the hacker name Khan K Smith. In this attack, he sent 1.25 millions emails from legitimate websites. From this attack, he gained the sensitive information like customer credit and bank account details. In the end, he earned $3 million from Earthlink Company with this attack and then Earthlink company sued him $25 million.
How to prevent the Botnet: Here are few steps to stop the botnet attacks
- Install window firewall on you system: User need to configure the window fire and always turn it on when possible.
- Disable Autorun: This feature will automatically run the software without user input. To prevent the botnet attacks, user need to disable this feature on their system.
- Secure the user information: All the account information like user passwords and ids should be confidential.
- Separate the departments: In small or large organization, employee should be work in departments. So, different departments can not accidentally pass the confidential information.
- Intrusion Detection System on host: IT administrator can use the advance security like Intrusion Detection system to stop the hacktivist. However, these type of tools are very expensive but its worthy to stop the attack.
- Increase Monitoring: Monitoring the regular activity of user is important part of security In future this can prevent the intrusion.
Credit Monitoring increase
- Stop the fake traffic: To stop the fake traffic, many tools like egress filtering are available in the market. This is effective tool to stop the fake traffic. Another services like Data Loss Prevention(DLP) or content filters are also useful.
- Proxy Servers: Proxy Servers play important role in blocking the traffic.
Source: https://securityintelligence.com/thingbots-the-future-of-botnets-in-the-internet-of-things/
Source: https://www.esecurityplanet.com/trends/article.php/3920881/11-Ways-to-Combat-Botnets-the-Invisible-Threat.htm

Comments
Post a Comment